
Unveiling Cryptojacking Attacks: Is Your Computer Secretly Mining Cryptocurrency?
In the shady corners of the internet, lurk cybercriminals always on the lookout for ways to steal your stuff. Cryptojacking might sound futuristic, but it’s a real threat that can hijack your computer’s power for their own gain. Cryptojacking attacks have become a prevalent threat in the world of cybersecurity, exploiting unsuspecting users’ computing resources to mine cryptocurrency without their consent.
What is Cryptojacking?
Cryptojacking is the unauthorized use of a victim’s computing resources to mine cryptocurrencies like Bitcoin, Ethereum, or Monero. Unlike traditional cyber attacks that aim to steal data or disrupt systems, cryptojacking attacks focus on leveraging the victim’s processing power to generate cryptocurrency for the attacker. Hackers, instead of buying their own expensive equipment, can use malware to secretly turn your computer into a crypto mining machine. This steals your processing power, slowing down your device and driving up your electricity bill, all while the attacker reaps the cryptocurrency rewards.
How Does Cryptojacking Work?
There are two main methods through which cryptojacking attacks are executed:
- In-browser Cryptojacking: This form of cryptomining works by loading malicious JavaScript code onto webpages, which runs in any browser that accesses the website. Attackers inject malicious code into websites, online ads, or browser extensions. When a user visits a compromised website or interacts with the infected content, the malicious code runs in the background, utilizing the victim’s CPU resources to mine cryptocurrency.
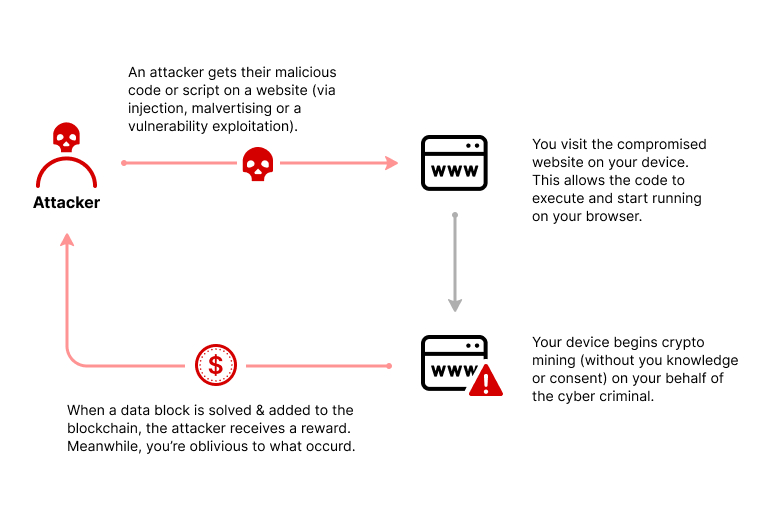
- Malware-based Cryptojacking: Attackers distribute malware through various vectors such as phishing emails, malicious downloads, or software vulnerabilities. Once installed on a victim’s device, the malware silently runs in the background, utilizing CPU or GPU resources to mine cryptocurrency without the user’s knowledge.
Cryptojacking Attacks

- Monero In-Browser Mining(Coinhive): In 2018, a popular JavaScript library called Coinhive was discovered to be incorporating cryptojacking code. Website owners could embed Coinhive’s JavaScript code into their websites, allowing them to mine Monero using visitors’ CPU resources. Many legitimate websites unknowingly used Coinhive, and visitors experienced degraded performance due to the excessive CPU usage.
- Popcorn Time Cryptojacking: The popular (but illegal) streaming service Popcorn Time was infiltrated with cryptojacking code in 2018, impacting millions of users.
- Tesla’s Cloud Infrastructure: In 2018, Tesla’s cloud infrastructure was compromised by attackers who deployed cryptojacking malware. The attackers exploited an unprotected Kubernetes console to gain access to Tesla’s Amazon Web Services (AWS) environment. They then deployed cryptojacking malware, which utilized Tesla’s cloud resources to mine cryptocurrency.
- WannaMine v4.0: WannaMine v4.0 is the latest iteration of the notorious WannaMine exploit tool, leveraging the EternalBlue exploit to compromise Windows hosts. What sets this version apart is its incorporation of a command and control (C&C) server, allowing attackers to issue instructions for malicious activities. WannaMine v4.0 can rapidly propagate across networks using lateral movement techniques, making it a formidable threat to distributed network infrastructures.
- Facexworm: Facexworm employs social engineering tactics to lure unsuspecting Facebook Messenger users into clicking on a fake YouTube link. Upon clicking the link, users are prompted to download a Chrome extension to view the content. However, this extension is malicious, allowing attackers to execute various malicious activities, including data theft and further propagation of the malware.
- Black-T: Black-T is a newly discovered malware targeting cloud-based Amazon Web Services (AWS) environments. Upon compromising a vulnerable AWS server, Black-T exploits exposed Docker daemon APIs to initiate a cryptojacking operation. By surreptitiously harnessing the computing resources of compromised servers, Black-T aims to mine cryptocurrency without the knowledge or consent of users, posing a significant threat to cloud infrastructure security.
- BadShell: BadShell represents a growing trend in malware development, characterized by its fileless nature. Unlike traditional malware, BadShell does not require victims to download any files to become infected. Instead, it leverages native Windows processes such as PowerShell, Task Scheduler, and the Windows Registry to execute its payload discreetly. This stealthy approach allows BadShell to evade detection by traditional antivirus software and pose a persistent threat to system security.
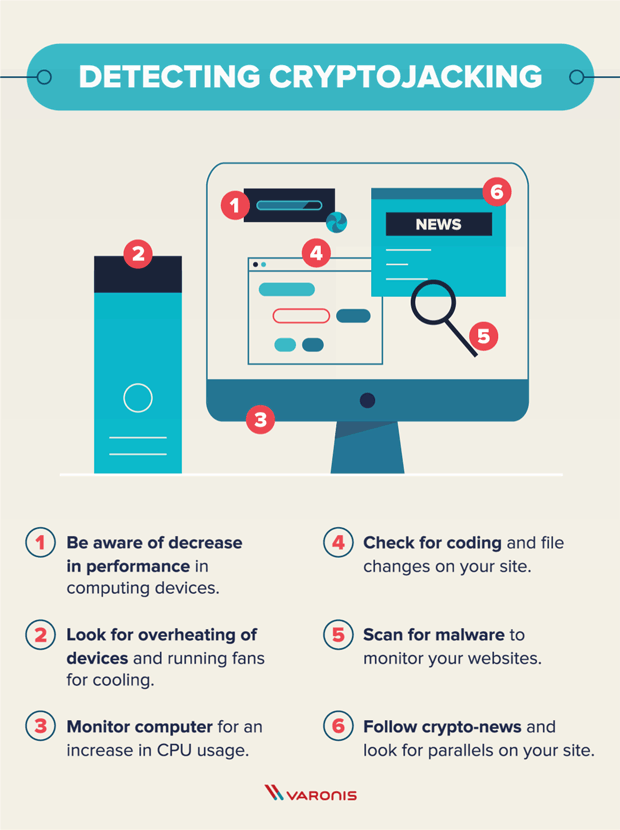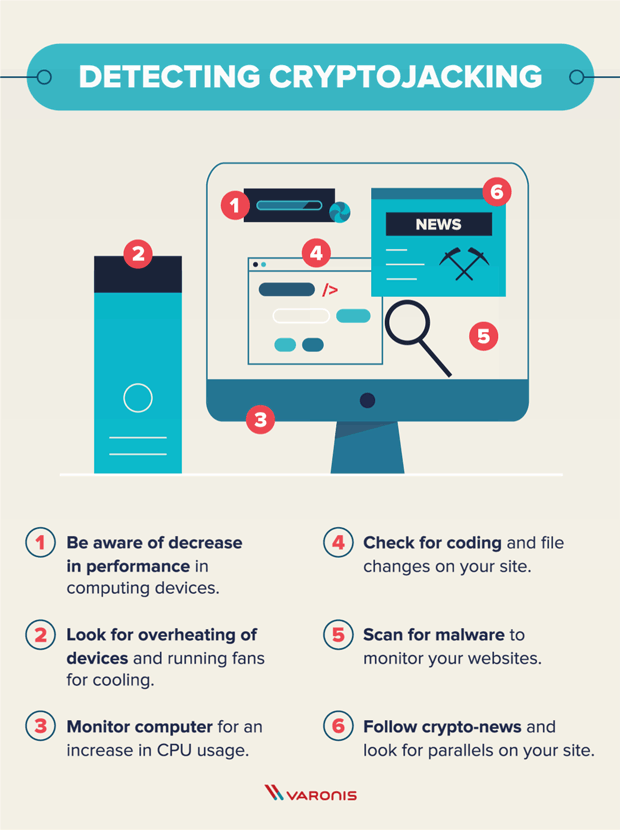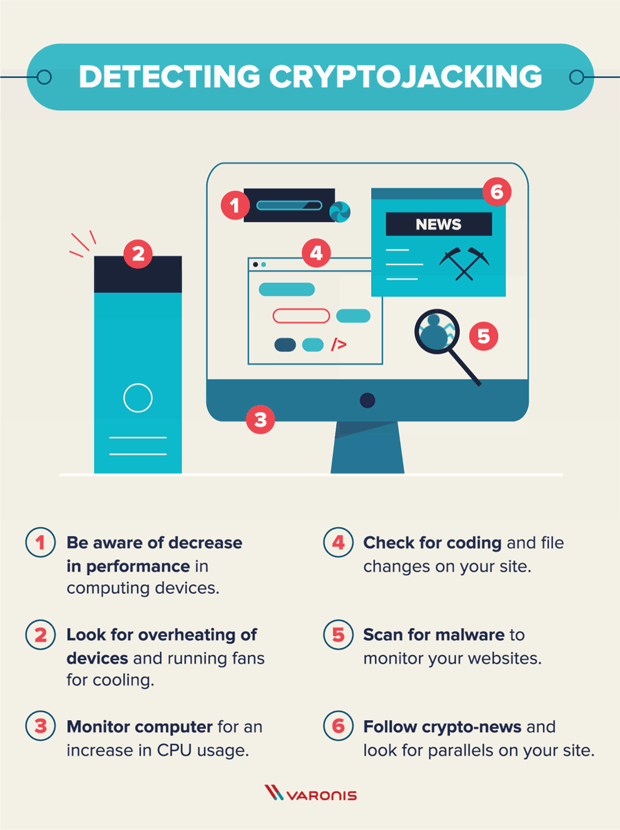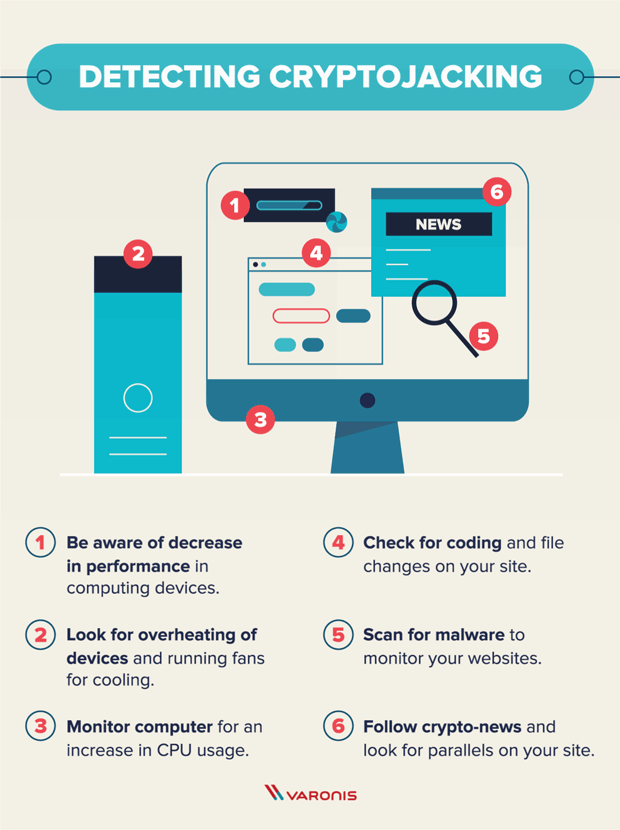
Cryptojacking attacks pose a significant threat to individuals and organizations, exploiting their computing resources for financial gain. By understanding how cryptojacking works and implementing appropriate security measures, you can protect yourself and your devices from falling victim to these stealthy attacks. Stay vigilant, stay informed, and safeguard your computing resources from cryptojackers.
Thank you for reading my blog. If you have any questions, feedback, or would like to share your thoughts on this topic, feel free to reach out to me. I value your input and would love to hear from you!
You can contact me via email at chethinell@gmail.com or connect with me on LinkedIn or X. Don’t hesitate to reach out — I’m here to help and engage in meaningful discussions about cybersecurity and technology.
Stay safe and secure online!